If you are
still having issues after all of this, try running
Autoruns. This nifty little program brings up a display of all the locations in
the registry and file system where programs can be set to start automatically on
boot up. Look though here for anything suspicious.
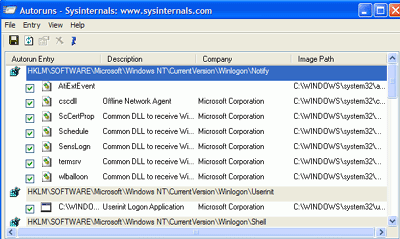
Suspicious files can be
anything you don't recognize. In this case, experimenting by unchecking
items will do no harm to your system, since these are only automatic startup
settings, not vital system files.
The next utility we look
will most certainly harm vital system files if used incorrectly.
Hijack this is a utility designed to counter browser-hijacking programs.
It displays several areas of the file system and registry related to the behaviour
of Internet Explorer.
It's intended
for advanced users, and simply displays the contents of these locations and
allows users to delete entries they do not think should be there. It makes
no attempt to distinguish vital
system files from entries placed by browser hijackers and malware. For
this reason, the best way to use Hijack This is to save a log file of the scan
results and post them onto one of many helpful forums along with a description
of your problem.
To do this:Run Hijack This and click
'scan.'
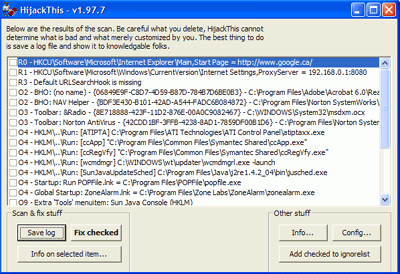
Scan through the results for
any obviously suspicious entries. Now
use the 'save log' button to save the results to a text file.
If you've followed the
directions above, chances are your PC is now free of its spyware problems.
Continue on for a guide to protecting your PC from futurer
infestation.

