
|
The security of computer systems is of major concern to all users. Millions of dollars are spent annually to reduce systems vulnerability. However, a cursory review of published reports reveals that losses due to intentional or unintentional security failures are increasing.
90% Rating: 
|
|
|
|
Home >
Reviews >
Peripherals >
Keyghost |
|
|
Operation
With its simple functionality, the KeyGhost II Pro is pretty easy
to use. Once you have opened a text editor, simply type in your password on the
following menu will appear...
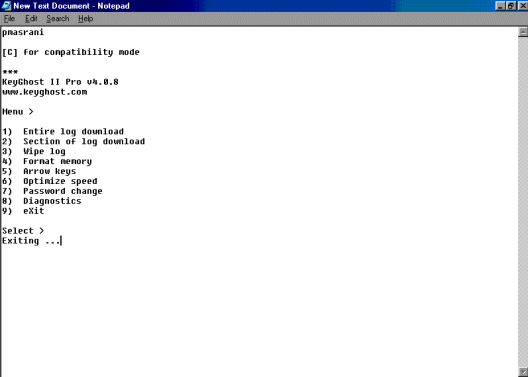
You will come up with a menu in which you can either view the
log in full or in part, change the password to access the menu, diagnose the
device, format the flash memory, wipe the log, and even specify whether or not
arrow keys are to be trapped.
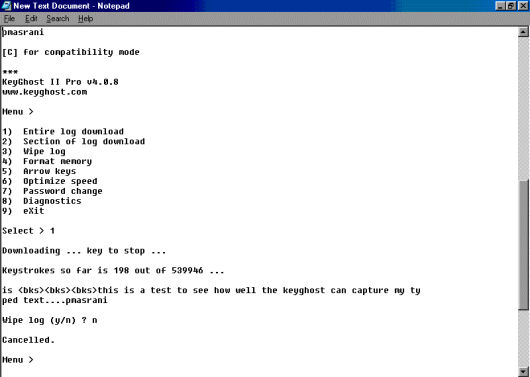
The output of the capture log includes
which arrow keys and other non ASCII keys that were typed. In case you cannot
interpret the symbols for such keys, all you have to do is look in the manual
and refer to the symbol in question.
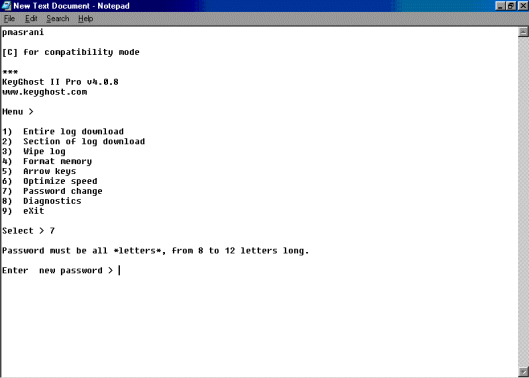
Changing the password is easy as well.
A screenshot of the diagnose function.
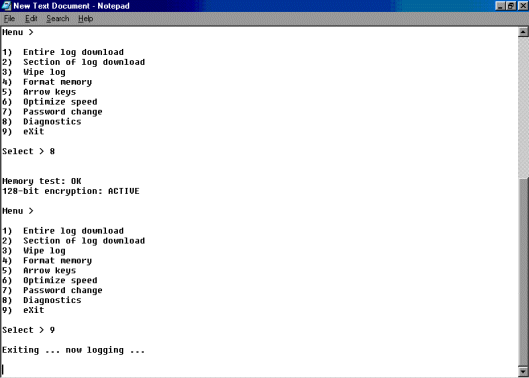
Yep, 128 bit
encryption!
|
