
|
This article aims to cover the basics of online
security, including a description of the methods online stores use to protect
themselves and their customers.
|
|
|
|
Home >
Reviews >
Beginners Guides >
PCSTATS |
|
|
Creating a recovery agent
Decide which user you wish to
use as a data-recovery agent. It is recommended that you use the built in
'administrator' account. Login as this account. Go to 'start\run' and type 'cmd' to bring up the command prompt.
Type 'cipher /r:(pick a
filename) to create a digital certificate for a recovery agent. You will be
prompted to set a password. This creates two files in the 'my documents' folder
of the current user. Be aware that these files can be used by anyone to become a
data-recovery agent, so it is wise to remove them after we are finished this
procedure.
Go to 'start\run' and type
certmgr.msc.
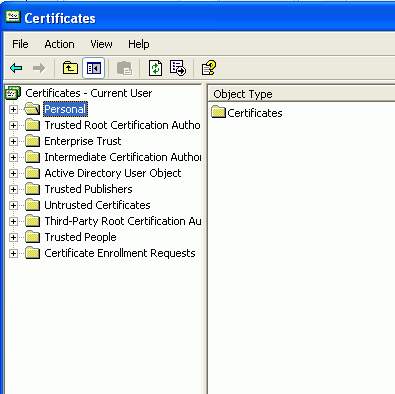
Go to 'certificates - current
user\personal' right click and choose 'all tasks' then 'import' Click
next.
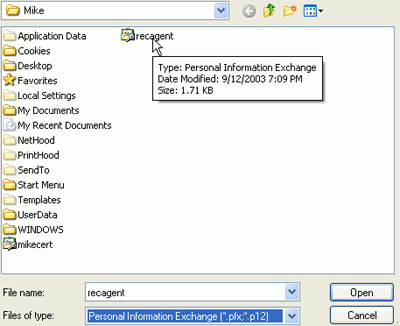
On the 'file to import' page,
click 'browse' then change the 'files of type' dropdown box to .pfx
files.
Select the filename you
created with the 'cipher /r:' command. Type the password. Check the 'mark this
key as exportable' box.
Click 'next.' Choose the
'Automatically Select The Certificate Store Based On The Type Of Certificate'
option. Click 'next,' then 'finish.' Close the certificates
console.
|
< Previous Page
|
© 2025 PCSTATS.com
Please respect the time and effort that went into creating each PCSTATS Beginners Guide, do not illegally copy. Thank you.
|
Next Page >
|
|

